Sleepy Pony @ Cyber Apocalypse 2024 CTF!
Vol 1: Maze and BunnyPass
Preface
This is my first time trying my hands on a CTF event: HackTheBox Cyber Apocalypse 2024! I'm no hacker, but this event has a hardware category, so my friend invited me to a team to try them out. It turned out better than I thought! I was able to solve all of the 5 hardware CTFs! And here's my writeup.
Maze - Very Easy
Problem Statement
In a world divided by factions, "AM," a young hacker from the Phreaks, found himself falling in love with "echo," a talented security researcher from the Revivalists. Despite the different backgrounds, you share a common goal: dismantling The Fray. You still remember the first interaction where you both independently hacked into The Fray's systems and stumbled upon the same vulnerability in a printer. Leaving behind your hacker handles, "AM" and "echo," you connected through IRC channels and began plotting your rebellion together. Now, it's finally time to analyze the printer's filesystem. What can you find?
What's Provided?
- One zip file
Capturing the Flag
Upon extracting the files, we found out that what we got is a filesystem archive of an HP printer.
HP ChaiServer Filesystem
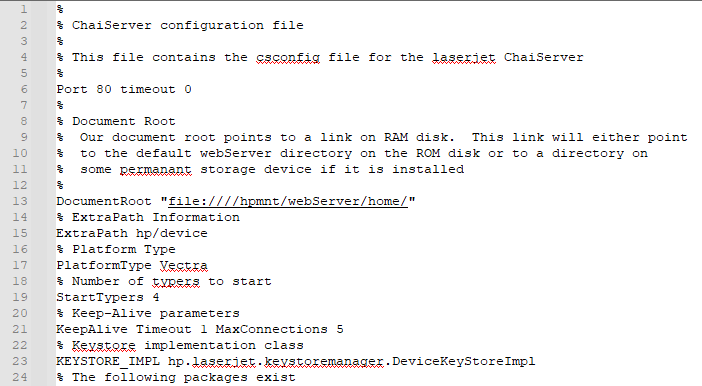
HP WebServer Config
After exploring the files a bit, we found an unfinished job in the fs/saveDevice/SavedJobs/InProgress directory: A PDF file Factory.pdf
A suspicious PDF file appears!
And what do we have here, the flag!
HTB{1n7323571n9_57uff_1n51d3_4_p21n732}

Here is our flag on the second page
Disclaimer: Stupid sleepy pony actually did not solve this one for the team. Someone did because the pony did not check to see if the PDF has multiple pages… pfff…
~~~~~
BunnyPass - Very Easy
Problem Statement
As you discovered in the PDF, the production factory of the game is revealed. This factory manufactures all the hardware devices and custom silicon chips (of common components) that The Fray uses to create sensors, drones, and various other items for the games. Upon arriving at the factory, you scan the networks and come across a RabbitMQ instance. It appears that default credentials will work.
What's Provided?
- A Docker instance
Capturing the Flag
Upon arrival at the specified web page, we arrived at a RabbitMQ login page. Since the problem statement said It appears that default credentials will work. a quick google search told us that the default credentials is
- Username = guest
- Password = guest

RabbitMQ Login Page
Thanks Google!
But what is RabbitMQ anyway?
To be short, RabbitMQ is an MQTT Broker. In contrast of a typical client-server architecture, MQTT uses a publish-subscribe architecture. This requires one server to act as a broker to facilitate message transfer from publishers to subscribers, based on topic of the messages. MQTT is popular in an IoT settings because you don't have to ping the server continuously for data. It's all event based!
Read more at rabbitmq.com and mqtt.org
OK, now what?
Since we know RabbitMQ is an MQTT broker, it must have message queues for storing the data published by the publishers, waiting to be sent to subscribers that are subscribed to the topic. Conveniently RabbitMQ has a GUI for us to query them right on the browser. Just go to Queues tab.
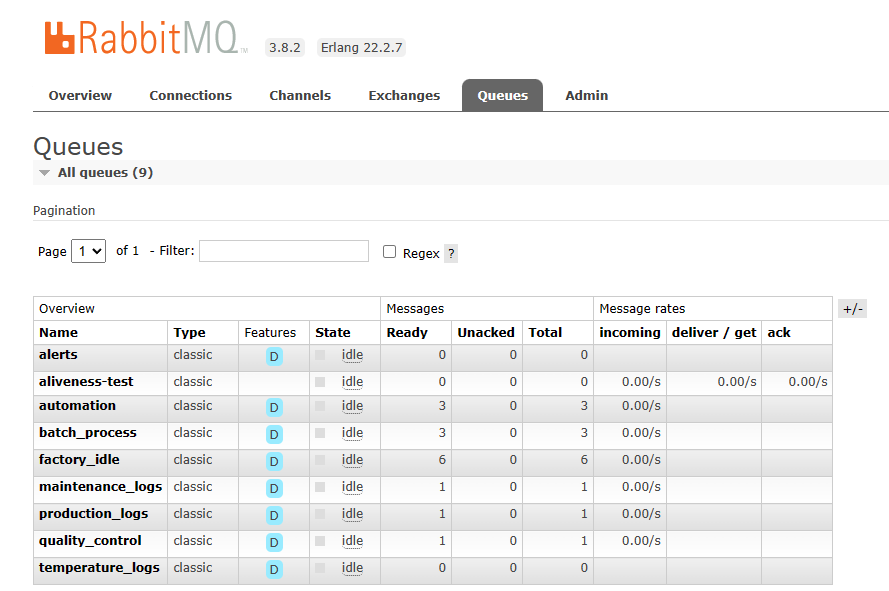
MQTT Message Queues on the Broker
Now we just go query up each topic, and in no time we found our flag in the factory_idle topic.
HTB{th3_hunt3d_b3c0m3s_th3_hunt3r}
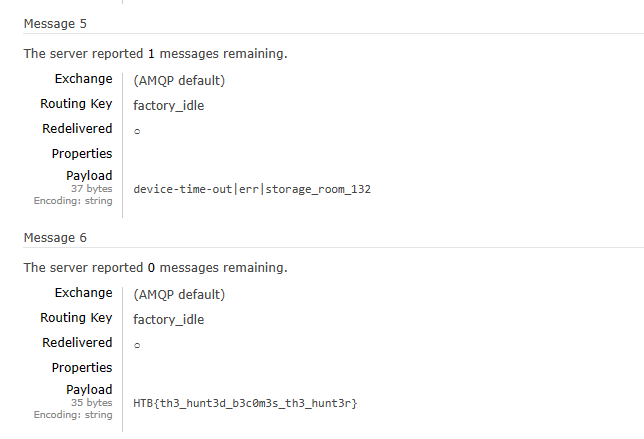
Here is our flag!
~~~~~